In today’s hyper-connected world, smartphones have become extensions of ourselves—silent companions that map our journeys, capture our memories, and even anticipate our needs. Yet, amidst this seamless integration lies a complex web of data trails and digital footprints that reveal more than we might intend. This dichotomy forms the crux of the privacy paradox in the mobile era: a landscape where the allure of convenience often clashes with the imperative of personal privacy. As users revel in the benefits of mobile technology, questions arise about the true cost of connectivity and the measures necessary to safeguard our most intimate data. Exploring this paradox unveils the delicate balance between embracing innovation and protecting the sanctity of our private lives.
Table of Contents
- Balancing Convenience and Confidentiality in Mobile Usage
- Understanding User Behavior to Enhance Privacy Protections
- Implementing Advanced Encryption Techniques for Mobile Data
- Building Trust Through Transparent Privacy Policies
- Navigating Regulatory Landscapes in the Mobile ecosystem
- Empowering Users with Control Over Their Personal Information
- In Summary

Balancing Convenience and Confidentiality in Mobile Usage
In todayS fast-paced world, mobile devices have become indispensable tools that streamline our daily activities, from managing schedules to accessing information on the go. This convenience, however, often comes at the cost of our privacy. Navigating this delicate balance requires a thoughtful approach to how we use our smartphones and the measures we take to protect our personal information.
One key strategy is to be mindful of the permissions granted to apps. While many applications request access to various aspects of your device to function optimally, not all permissions are necessary. By regularly reviewing and adjusting app permissions, users can limit the amount of data shared unintentionally.Additionally, leveraging built-in privacy settings and utilizing encryption can further safeguard sensitive information from potential breaches.
The following table highlights common mobile features and tips to enhance privacy without sacrificing functionality:
| mobile Feature | Privacy Tip | Convenience Impact |
|———————-|——————————————|—————————–|
| Location Services | Enable onyl when necessary | Slight reduction in app utility|
| App permissions | restrict non-essential access | Enhanced data security |
| Data Synchronization | Use encrypted services or selective sync | Maintains accessibility while protecting data|
| public Wi-Fi Usage | Utilize VPNs to secure connections | Ensures safer browsing on the go|
By adopting these practices, users can enjoy the benefits of mobile technology while maintaining control over their personal information. Striking the right balance between convenience and confidentiality is essential in mitigating the privacy paradox inherent in the mobile era.
Understanding User Behavior to Enhance Privacy Protections
In the mobile era, users interact with their devices in diverse and dynamic ways.By delving into these interactions, organizations can gain valuable insights into user behavior, which are pivotal for crafting robust privacy protections.Understanding patterns such as app usage frequency, data sharing preferences, and response to privacy settings enables companies to anticipate potential vulnerabilities and address them proactively.
Consider the following table, which highlights common user behaviors and corresponding privacy enhancement strategies:
| User Behavior | Privacy Enhancement Strategy |
|—————————–|—————————————————|
| Frequent App Switching | Implement seamless data encryption across apps |
| Reluctance to Adjust Settings | Simplify privacy settings with intuitive controls |
| high Data sharing for Convenience | Offer granular permission options |
| Limited Awareness of Data Usage | Educate users through transparent policies |
By aligning privacy measures with actual user behaviors, companies not only safeguard sensitive information but also foster trust and reliability. This user-centric approach ensures that privacy protections are both effective and aligned with the real-world usage patterns of mobile device owners.Ultimately, leveraging behavioral insights bridges the gap between user expectations and security imperatives, navigating the privacy paradox with informed precision.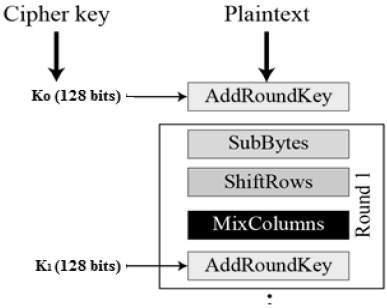
Implementing Advanced Encryption Techniques for Mobile Data
In the mobile era, safeguarding data has become paramount. Advanced encryption techniques serve as the frontline defense against unauthorized access, ensuring that personal and sensitive information remains secure. By integrating robust encryption protocols, mobile applications can protect user data from potential breaches, weather the threat comes from cybercriminals or unintended data leaks.
One effective method is the implementation of end-to-end encryption (E2EE), which ensures that data is encrypted on the sender’s device and only decrypted on the recipient’s device. This process makes interception efforts futile,as the data remains unreadable during transmission. Additionally, adopting symmetric and asymmetric encryption algorithms, such as AES and RSA, respectively, can provide layered security, addressing different aspects of data protection.
Moreover, leveraging encryption standards like Transport Layer Security (TLS) and Secure/Multipurpose Internet Mail Extensions (S/MIME) can enhance the overall security posture of mobile applications. Regular updates and adherence to best practices in key management are essential to maintaining the effectiveness of these encryption techniques. Below is a table summarizing some advanced encryption methods commonly used in mobile data protection:
| Encryption Technique | Description | Use Case |
|———————-|———————————————|———————————–|
| AES (Advanced Encryption Standard) | Symmetric encryption algorithm | Data storage and transmission |
| RSA (Rivest–Shamir–Adleman) | asymmetric encryption algorithm | Secure key exchange |
| E2EE (End-to-End encryption) | Ensures data is encrypted on sender and decrypted only by recipient | Messaging and communication apps |
| TLS (Transport Layer Security) | Protocol for secure communication | Protecting data in transit |
By strategically implementing these advanced encryption techniques,mobile developers can navigate the complexities of data privacy,ensuring that users’ information remains confidential and secure in an increasingly connected world.
Building Trust Through Transparent Privacy Policies
In the mobile era, where data breaches and privacy concerns are increasingly prevalent, establishing trust with users is paramount. Transparent privacy policies act as a bridge between app providers and users, clearly communicating how personal information is collected, used, and protected. By demystifying data practices, companies can alleviate fears and foster a sense of security among their audience.
A well-articulated privacy policy not only ensures compliance with regulations but also demonstrates a company’s commitment to ethical data handling. When users are informed about the specifics of data usage, they are more likely to engage confidently with the app. Transparency in privacy policies builds a foundation of trust, encouraging long-term user loyalty and positive brand reputation.
Essential Components of an Effective Privacy policy
| Component | Purpose |
|——————–|———————————————-|
| Data Collection | Clearly state what information is gathered |
| Data Usage | Explain how the collected data is utilized |
| Data sharing | Specify if and with whom data is shared |
| User Rights | Outline users’ control over their personal data |
| Security Measures | Describe the protections in place to safeguard data |
By incorporating these elements, businesses can create comprehensive and user-pleasant privacy policies. This transparency not only helps navigate the complexities of the privacy paradox but also positions the company as a trustworthy and user-centric entity in the competitive mobile landscape.
Navigating Regulatory Landscapes in the mobile Ecosystem
As the mobile ecosystem continues to expand, so does the complexity of its regulatory surroundings. Companies must adeptly navigate a patchwork of local and international laws to ensure compliance and protect user privacy. This involves staying informed about emerging regulations and adapting business practices to meet diverse legal requirements.
One critical aspect is understanding data protection laws, such as the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the United States. These regulations mandate strict guidelines on data collection, storage, and usage, compelling organizations to implement robust privacy measures. Failure to comply can result in hefty fines and reputational damage, making regulatory adherence not just a legal obligation but a strategic priority.
Moreover, the dynamic nature of technology means that regulations are continually evolving to address new privacy challenges. Mobile companies must foster a culture of compliance, investing in legal expertise and adaptive technologies to anticipate and respond to regulatory changes. Collaboration with policymakers and industry stakeholders can also facilitate the development of balanced regulations that protect users while fostering innovation.
Key Mobile Regulations Overview
| Regulation | Region | Main Focus | Enforcement Body |
|——————|—————-|———————————|————————–|
| GDPR | europe | Data protection & privacy | European Data Protection Board |
| CCPA | California, USA | Consumer data rights | California Attorney general |
| PDPA | Singapore | Personal data protection | Personal Data Protection Commission |
| LGPD | Brazil | Data privacy and protection | National data Protection Authority |
Empowering users with Control Over Their Personal Information
in the bustling landscape of the mobile era, users frequently enough find themselves at the crossroads of convenience and privacy. Empowering individuals to take charge of their personal information is not just a necessity but a basic right. By understanding the tools and strategies available, users can navigate their digital lives with confidence and security.
Key Strategies for Personal Information Control
| Strategy | Description |
|—————————-|———————————————————————————|
| Privacy Settings Audit | Regularly review and adjust app permissions to limit data access. |
| utilize Encryption | Protect sensitive data with end-to-end encryption on messaging and storage apps.|
| Awareness of Data Trails | Understand how and where your data is being collected and used. |
| Adopt Privacy-Focused Apps | Choose applications that prioritize user privacy and transparent data policies. |
Taking proactive steps, such as conducting a privacy settings audit, can considerably reduce unwanted data exposure. Users are encouraged to leverage encryption tools to safeguard their communications and personal files. Additionally, fostering an awareness of data trails helps in making informed decisions about the information shared online.
Moreover, the adoption of privacy-focused applications serves as a powerful means to reclaim control. These apps are designed with stringent data protection measures,ensuring that user information remains confidential. By embracing these practices, individuals can effectively balance the benefits of mobile technology with the assurance of their personal privacy.
In Summary
As we stand at the crossroads of connectivity and confidentiality, the privacy paradox in the mobile era challenges us to rethink our relationship with technology. Balancing the allure of seamless integration with the imperative of safeguarding personal information is no small feat. Yet, by fostering a deeper understanding and embracing thoughtful solutions, we can navigate this intricate landscape with both awareness and agency. In this dance between innovation and introspection, the path forward lies in informed choices and collective duty, ensuring that our mobile experiences enrich rather than compromise our sense of privacy.